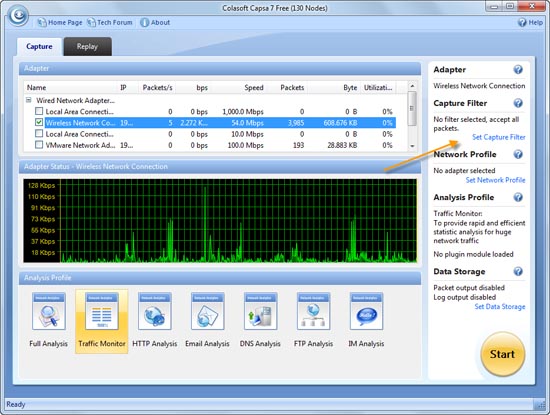
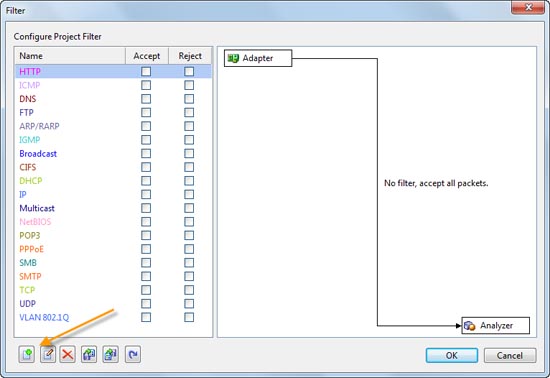
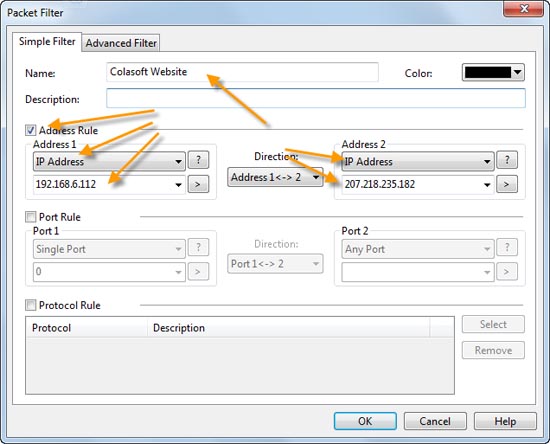
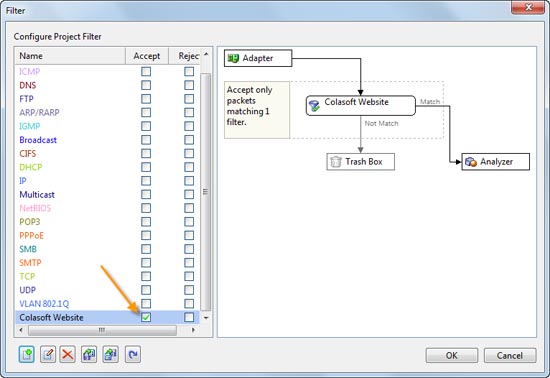
It’s always a challenge for IT departments to anticipate how corporate technical demands will evolve, especially when IT budgets have been as tight as a drum for two years.
How do you “do more with less” and prepare for an explosion in bandwidth demand, a need to upgrade both software and hardware, and employees asking that work data be available on their personal smartphones?
The post-recession enterprise IT environment is only going to get more chaotic, but opportunities abound for the savvy IT manager, according to a new report from Technisource, a technology staffing and services company with clients ranging from the mid-market to global Fortune 500 companies.
The pressure to have “efficient operations and visibility into every aspect of the organization despite strict budget constraints has been the genesis of strategic trends that are re-shaping IT priorities, whether you are supporting an online retail portal, a university, or a high-tech manufacturing operation,” writes report authors Andrew Speer, Chad Holmes and Dick Mitchell.
Here are four trends Technisource says will play a key role in defining your organization’s priorities for the next year or more.
1. You’re Gonna Need More Bandwidth
It’s almost a guarantee that organizations of all sizes will increase bandwidth in 2011 and 2012 to support growing multimedia within the corporate network. The main technologies driving this need are video conferencing and tele-presence, VoIP and distributed storage networks.
The smart IT manager will stay ahead of the bandwidth curve by assessing WAN and LAN environments frequently and looking for ways to save money.
“Regularly review WAN options, with special emphasis on emerging access technologies that offer better deals on bandwidth and flexible provisioning plans,” the Technisource report states.
“On the LAN side, pay attention to your cabling plant as well as your switch and router fleet to ensure that there are no hidden bottlenecks to impede the inevitable upgrades you’ll be making.”
2. Prepare for More Mobility and User-Owned Devices
Mobile business apps are no longer a luxury, but a necessity at every level of the organization. Advances in Wi-Fi and other wireless technologies can put much of the corporate network in a worker’s pocket. Handheld devices are now commonly used to access corporate e-mail and sales reports, and track supply chain inventory in real time.
Looking ahead, Technisource predicts companies will establish their own internal “apps stores” that give employees password-protected access to software tools and other corporate resources.
IT departments should also prepare to use mobility asset management software to remotely configure and upgrade mobile apps and secure lost or stolen mobile devices by remotely wiping them clean of sensitive data. Finally, network and security admins must prepare for the inevitable: corporate users requesting to use their personal iPhones, Droids and other consumer-friendly smartphones for work purposes.
3. Ascending to the Cloud, One Careful Step at a Time
Companies are slowly but surely moving to some sort of cloud computing model. According to Gartner Group research, 8% of U.S. corporations had implemented a cloud service at the end of 2010, and Gartner expects that number to jump to over 50% by the end of 2012.
A cloud model offers obvious benefits: cheaper pay-as-you-go delivery methods, less operational complexity and fewer, if any, servers to manage.
But a cloud migration is complex, particularly at the enterprise level where data security is paramount.
“You’ll need to develop heightened level of data security for the cloud computing environment, where some, or all, of your critical data resides outside the traditional corporate firewall,” the Technisource report states, adding that cloud-based apps are also not as flexible, providing users with only a simplified menu of configuration and control options.
“Expect some snags when integrating several applications from different vendors into the seamless cloud platform of your dreams,” the report states.
As for return on investment guidance: Technisource writes that initial cloud ROI gain is in the first two years due to a decrease in infrastructure costs, but fee structures should be reviewed in the third year to make sure you’re getting the best deal.
4. The Windows 7 Upgrade Catch-Up
For most businesses, the Great Recession put a hold on any non-essential technology upgrades. But the standard four-year refresh cycles are timing out and hardware and software are getting long in the tooth, to the point where user productivity is sapped and security is at risk.
While users with old PCs obviously need newer and faster hardware, the main driver for upgrades in 2011 is to migrate from Windows XP to Windows 7-capable PCs.
“In 2009 only 7% of businesses had adopted Windows 7, or planned to do so over the next 12 months,” the Technisource report states, “but this has skyrocketed to 46 % in 2010.”
But migrating a large installed base of Windows XP machines to Windows 7 is an IT resource drain and a complicated process that includes re-loading user data, applications, drivers, preferences and settings.
By Shane O’Neill from arnnet.com.au