Colasoft Announces Capsa Data Packet Analyzer v7.8 Release
August 20, 2014– Colasoft, an Oklahoma company, is a leading provider of innovative, affordable, network analysis software solutions. Colasoft today announced the release of its latest Capsa Network Analyzer, version 7.8, a real-time portable network analyzer for wired and wireless network monitoring, bandwidth analysis, and intrusion detection.
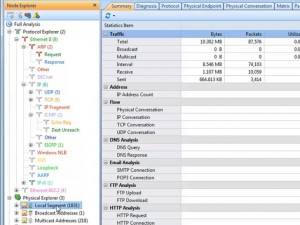
In addition to Bandwidth Monitoring and Traffic Analysis, Capsa Enterprise has added full support for VoIP communication analysis. Capsa customers can now, not only monitor VoIP calls, but also drill into a vast collection of call statistics detailing their jitter, loss, and MOS. The new VoIP Explorer and VoIP Diagnostic views allow users to visualize the VoIP data as Capsa visually displays the voice and video quality, assisting users in troubleshooting VoIP networks, software and hardware.
Colasoft has also added a new detailed Port Analysis view to their Capsa Enterprise packet capture application. This new Port Analysis view is quite useful in the analysis of application management issues to determine where the problem actually originates.
In addition to VoIP, Colasoft has added a new “Top Domain Name” view of the network traffic. Colasoft users can now view the traffic utilization by Domain Name in addition to IP Address. Additionally, this new release of Capsa Enterprise has added full support of IMAP4 to the hundreds of already supported protocols. A Free Trial version is available for download at: http://www.colasoft.com/download/products/download_capsa.php
With the increasing number of companies being hacked, Colasoft has seen a dramatic increase in the interest of its Capsa and nChronos products. As noted by Brian K. Smith, Vice President at Colasoft LLC, “Capsa is the only Packet Sniffer and Packet Decoder to provide an easy to use GUI combined with CyberAttack Detection features that were previously found only in more expensive Intrusion Detection Applications. Colasoft Capsa now offers the Network Engineer one of the most robust Bandwidth and Packet Analysis tools available.”
With the release of Capsa 7.8 there is now added support for protocols like: IMAP4, SIP, SDP, MEGACO/H.248, MGCP, Q.931, SAP, H.225, RMI, Oracle, MMS, GOOSE, SMV, and GMRP. Capsa also added several new VoIP protocols. Capsa inherently analyzes VoIP issues, like voice quality QOS, dropped packets and connectivity issues.
Capsa 7.8 is compatible with Windows XP/2003/2008/Vista/Windows 7/Windows 8 and Windows Server 2012. A trial version is available for download at: http://www.colasoft.com/download/products/download_capsa.php