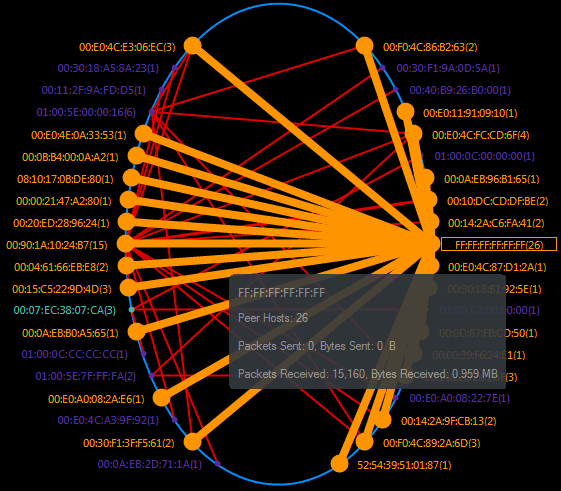
HOW TO DETECT ARP ATTACKS & ARP FLOODING WITH COLASOFT CAPSA NETWORK ANALYZER
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts byusing their MAC address and responding on their behalf, while at the same time flooding the network with ARP requests. ARP attacks are frequently used for ‘Man-in-the-middle‘ attacks, causing serious security threats, loss of confidential information and should be therefore quickly identified and mitigated.
During ARP attacks, users usually experience slow communication on the network and especially when communicating with the host that is being targeted by the attack.
In this article, we will show you how to detect ARP attacks and ARP flooding using a network analyzer such as Colasoft Capsa.
Colasoft Capsa has one great advantage – the ability to identify and present suspicious ARP attacks without any additional processing, which makes identifying, mitigating and troubleshooting much easier.
Download your copy of Colasoft Capsa and discover how easy it is to identify network & security related problems.
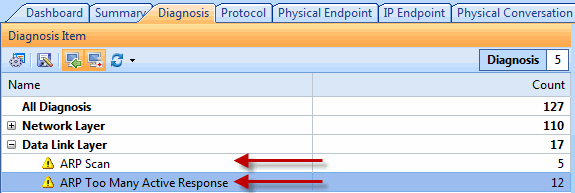
The Diagnosis tab provides real-time information and is extremely handy in identifying potential threats, as shown in the screenshot below:
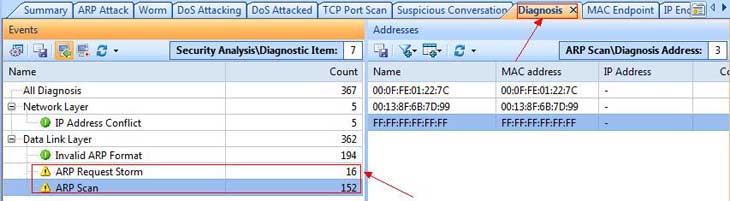
Figure 1. ARP Scan and ARP Storm detected by Capsa’s Diagnosis section.
Under the Diagnosis tab, users can click on the Events area and select any suspicious events. When these events are selected, analysis of them (MAC address information in our case) will be displayed on the right as shown above.
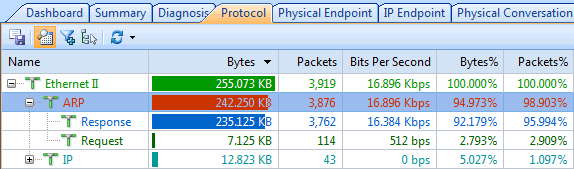
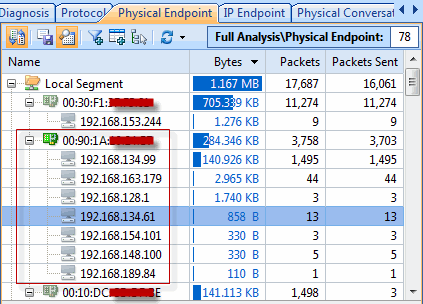
In addition to the above analysis, Capsa also provides a dedicated ARP Attack tab, which is used to verify the offending hosts and type of attack as shown below:
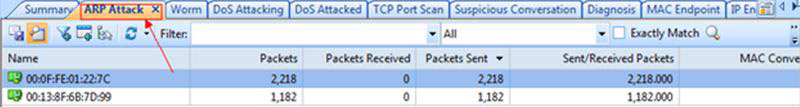
Figure 2. ARP Attack tab verifies the security threat.
We can extend our investigation with the use of the Protocol tab, which allows us to drill into the ARP protocol and see which hosts MAC addresses are involved in heavy ARP protocol traffic:
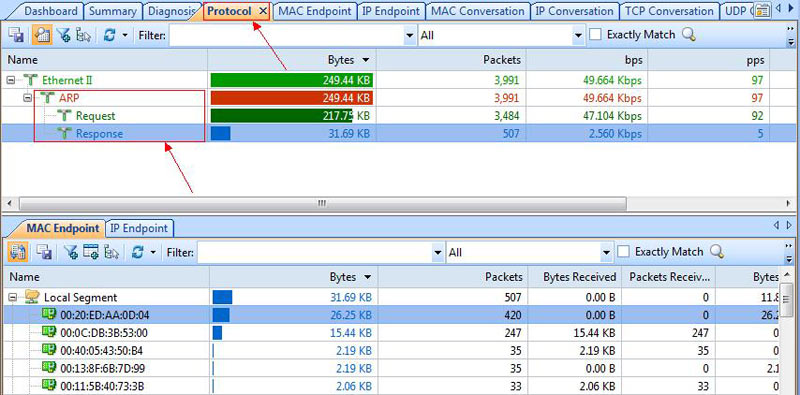
Figure 3. Drilling into ARP attacks.
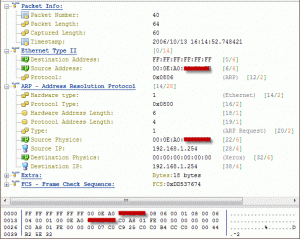
Finally, double-clicking on a MAC address in the ARP Protocol section will show all packets related to the selected MAC address.
When double-clicking on a MAC address, Capsa presents all packets captured, allowing us to drill-down to more useful information contained in the ARP packet.
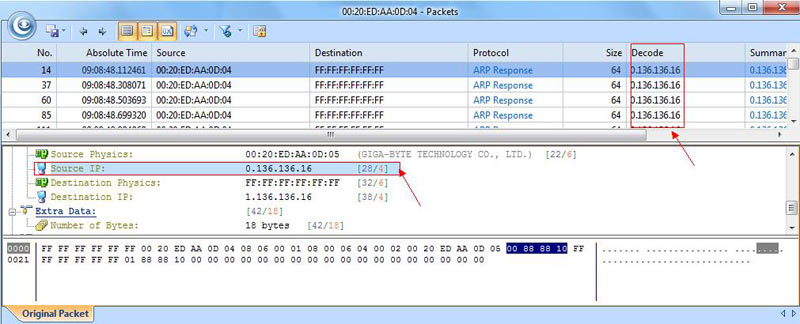
Figure 4. Drilling-down into the ARP attack packets.
By selecting the Source IP, in the lower window of the selected packet, we can see the fake IP address 0.136.136.16. This means that any host on the network responding to this packet will be directed to an incorrect and non-existent IP address, indicating an ARP attack of flood.
Download your copy of Colasoft Capsa and discover how easy it is to identify network & security related problems.
If you’re a network administrator, engineer or IT manager, we strongly suggest you try out Colasoft Capsa today and see how easy you can troubleshoot and resolve network problems and security threats such as ARP Attacks and ARP Flooding.