Review: Colasoft Capsa from WindowsITPro.com
by Michael Dragone at June 1, 2010.
At some point in the career of almost any IT professional, there comes a time when a detailed examination of network traffic at the packet level is required to troubleshoot a problem. These problems often occur at the worst time, and having the ability to quickly perform a detailed traffic analysis is critical to resolving the problem swiftly and efficiently.
In the field of network analyzers, there’s a range of choices. On the one end, you can obtain free tools that support basic capture tasks but require you to perform much of the analysis. On the other end, you can purchase multifunctional tools that perform the analysis for you.
I took at look at the recently released Capsa 7.1 from Colasoft to see how it performed. I was especially interested to see how it fared against free tools such as Microsoft’s Network Monitor and Wireshark (formerly Ethereal). I ran the software on a Windows XP Professional SP3 computer.
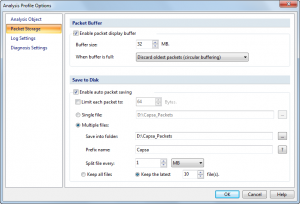
Capsa downloaded quickly, and the installation process was brief. During installation, I was given the opportunity to install additional Colasoft tools such as a packet generator. I declined because I was focusing on the network analyzer, but it was nice to see those tools included as an installation option and not as an additional download. I was also happy that the installation process gave me full control over the creation of the desktop and Quick Launch icons instead of littering my test computer with icons everywhere. Finally, I was expecting to have to reboot my computer after the installation, as I assumed that the installation routine would make changes to the network stack. I was happy to see that this wasn’t the case and no reboot was required.
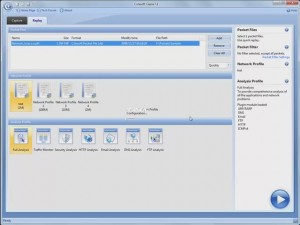
When you start Capsa, an interface presents you with intuitive options that let you select the network you want to analyze and the type of analysis you want to perform, such as Full Analysis, Traffic Monitor, Security Analysis, and Email Analysis. I wanted to analyze traffic, so I selected Traffic Monitor and clicked the large play button. The analysis began immediately.
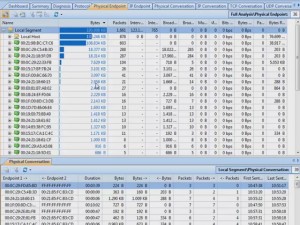
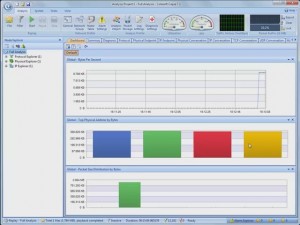
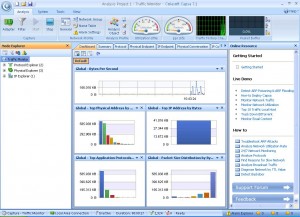
As Figure 1 shows, Capsa uses the Fluent interface introduced in Microsoft Office 2007. As such, it’s extremely easy to navigate and almost, dare I say, fun to poke around the various tabs as the product captures network traffic.
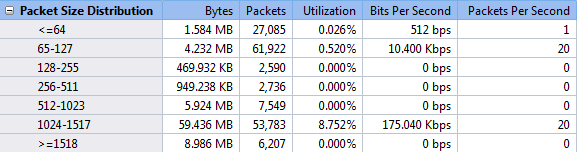
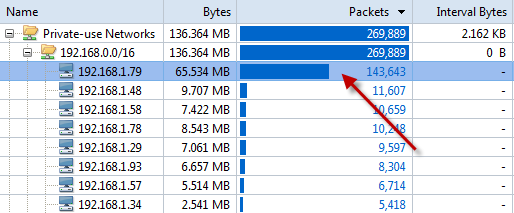
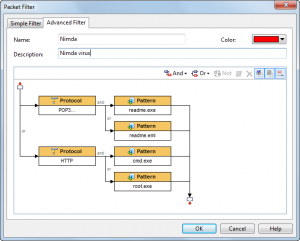
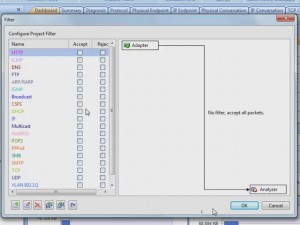
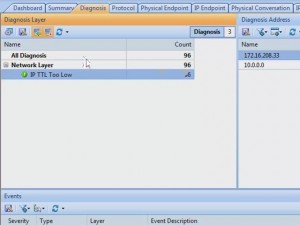
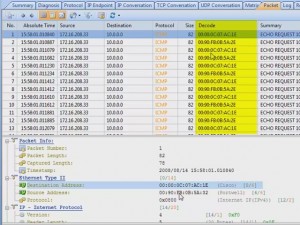
The information that the product can capture can be daunting, but it was easy to filter the capture to look for only HTTP traffic. The filter interface provides an excellent graphical representation of what your newly created filter will do.
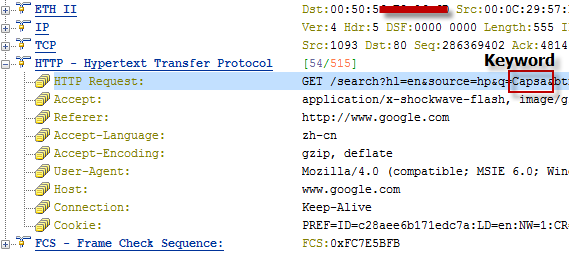
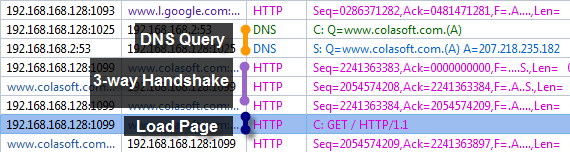
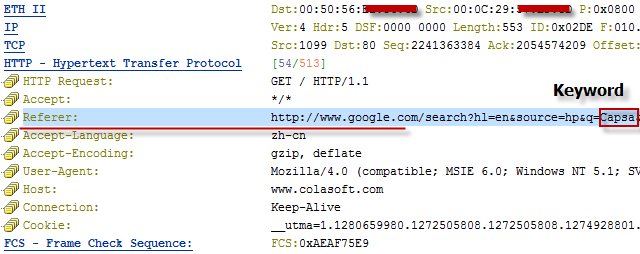
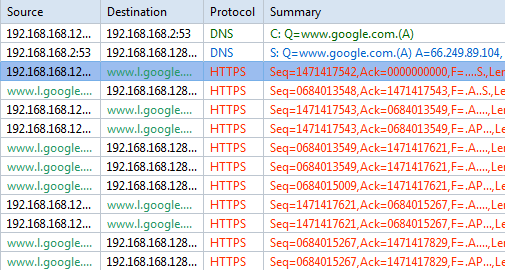
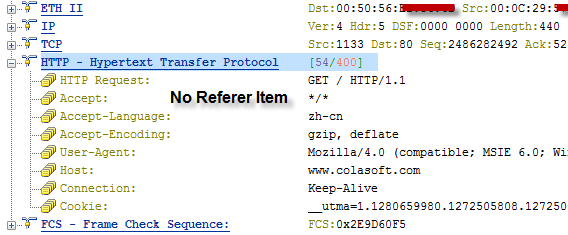
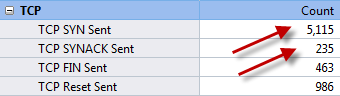
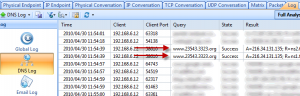
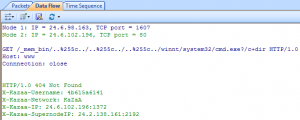
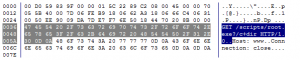
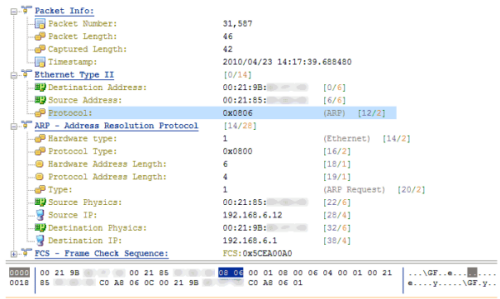
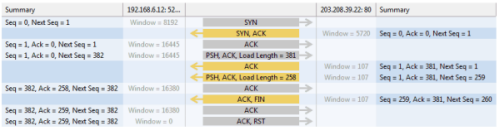
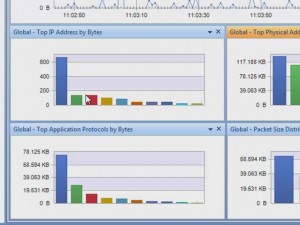
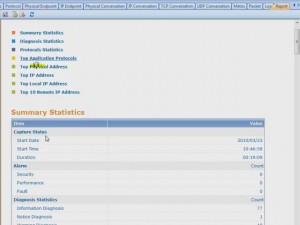
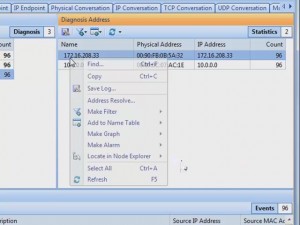
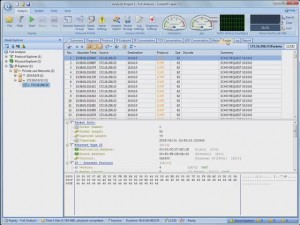
I was able to drill-down into my newly captured HTTP traffic to the packet level and examine all the details. Because it was encrypted HTTP Secure (HTTPS) traffic, I couldn’t look into the data payload, but all the header details were available. I was also able to examine entire TCP conversations, from the initial handshake all the way down to the FIN flag. The graphical representations that this product can produce are simply wonderful.
Overall, Capsa is a joy to use. My only complaint is the high price tag, which might make it difficult to obtain if you don’t spend a majority of your time examining network traffic, as free (and excellent) alternatives exist. Despite this, I highly recommend this product and would be glad to add it to my toolbox.