ITWire: Review – Colasoft Capsa network analyser
by David M Williams
July 26, 2010
If you run any type of network infrastructure there will come a time you need a low-level packet sniffer to work out just what is going on. Colasoft’s Capsa product challenges the myth these tools must be hard to use.
Have you ever had users ask why is the network so slow? Chances are high any IT professional will have looked into network related faults but found it difficult to get a handle on just what is going on because Ethernet is so, well, ethereal.
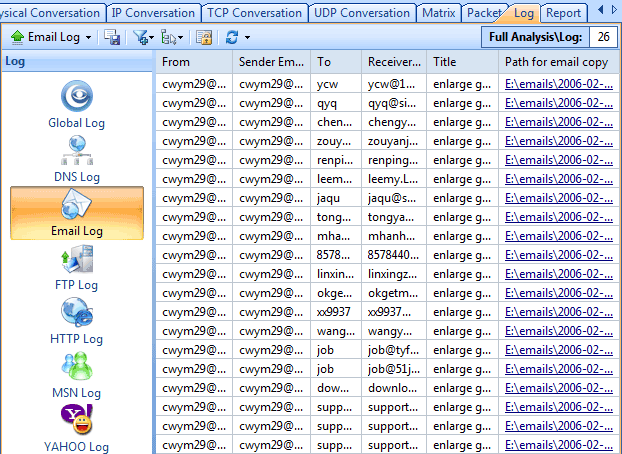
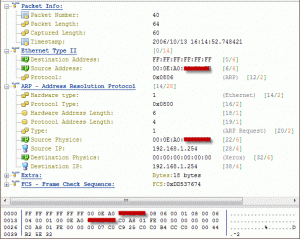
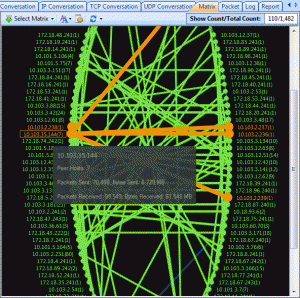
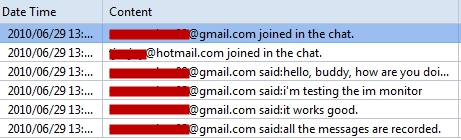
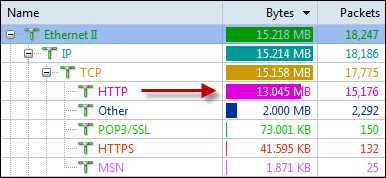
Here is where a network analyzer comes in handy. It will sniff the raw packets of data flying about as they happen and give you meaningful information to make intelligent determinations.
Previously I have talked about the tremendous open source product WireShark but WireShark isn’t for everyone. For one, the Windows port requires GTK+ and Glib to be installed which some Windows administrators aren’t keen to do. For another, although it is less arcane and cryptic than a command-line tool like tcpdump it’s still not user-friendly enough for many.
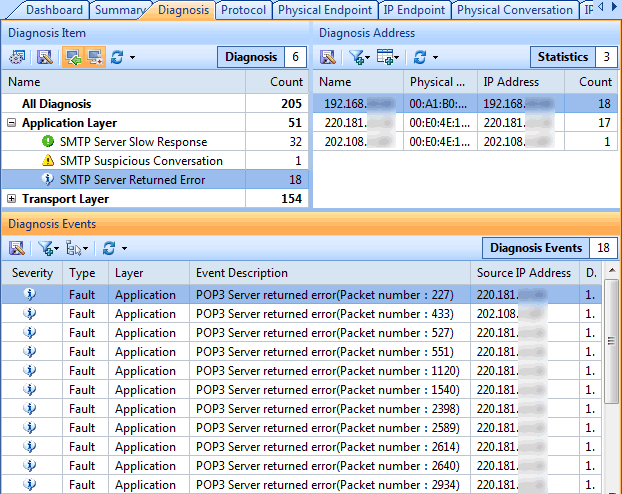
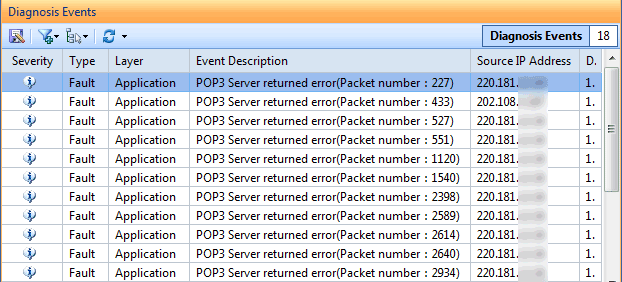
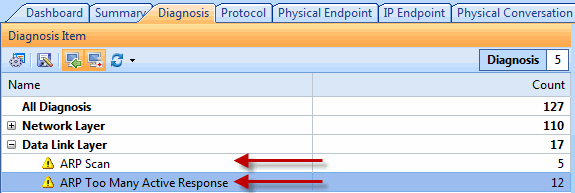
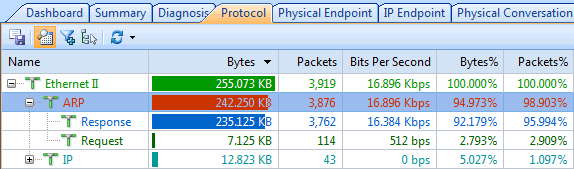
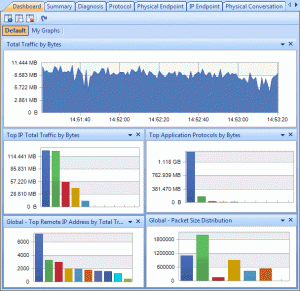
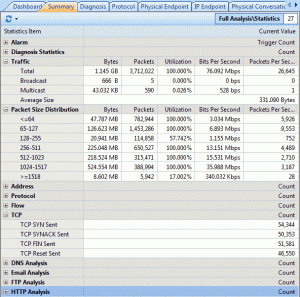
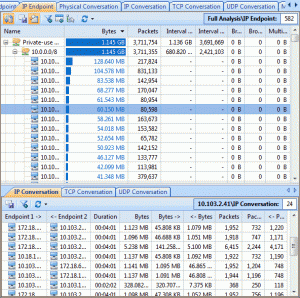
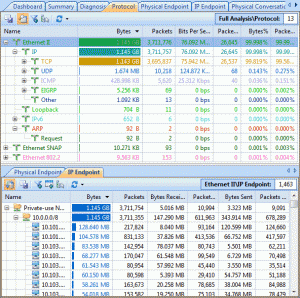
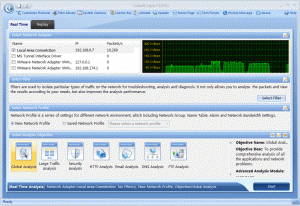
Here is where Colasoft’s Capsa product comes in. As you might guess, it is a deep low-level network protocol analyzer and its purpose is to give you the low-down on just what is happening on your network.
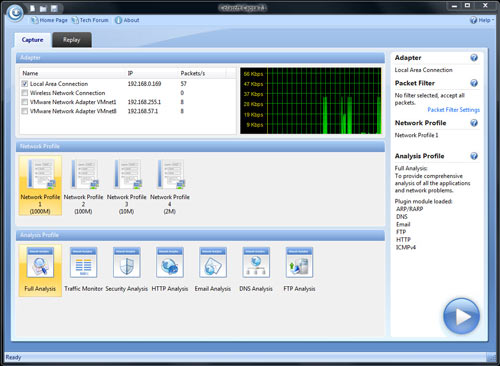
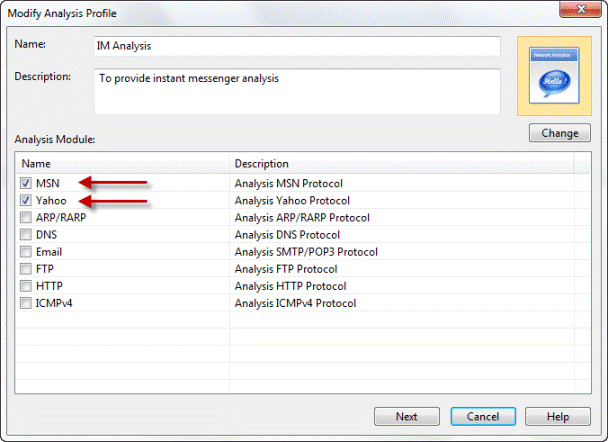
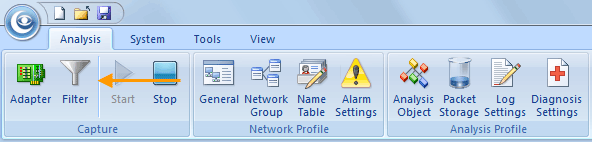
Where it stands out from the competition is its brilliant ease of use. Capsa adopts the same ribbon style interface as seen in Microsoft Office 2007 and it is a snap to navigate between tabs and check out the options and power available.
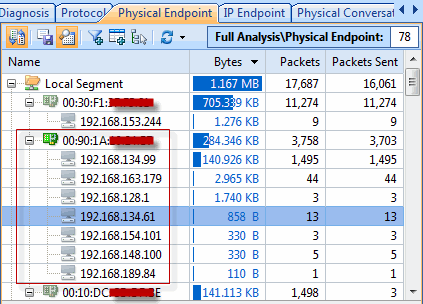
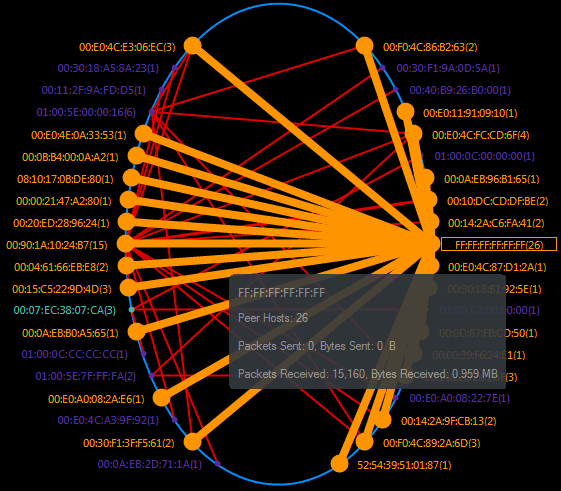
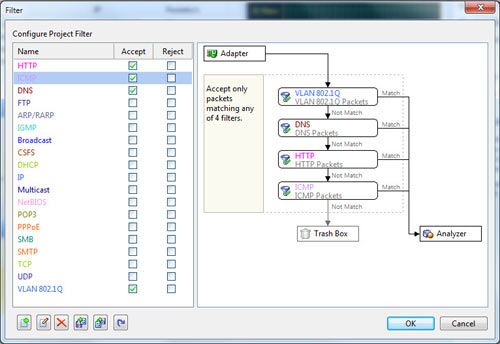
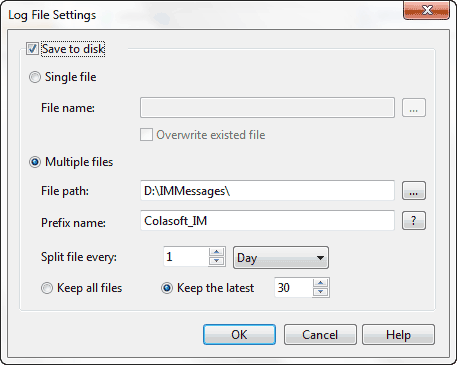
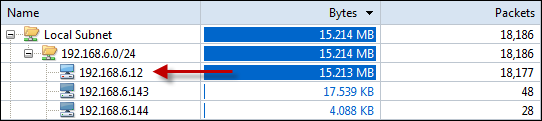
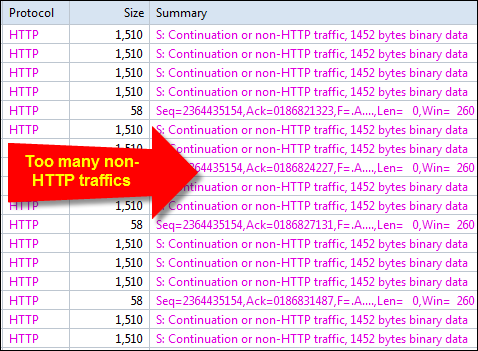
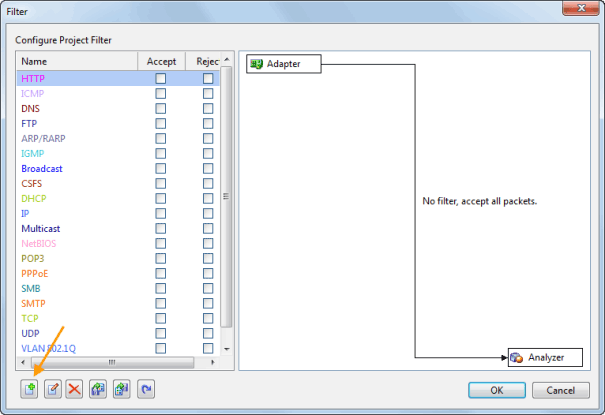
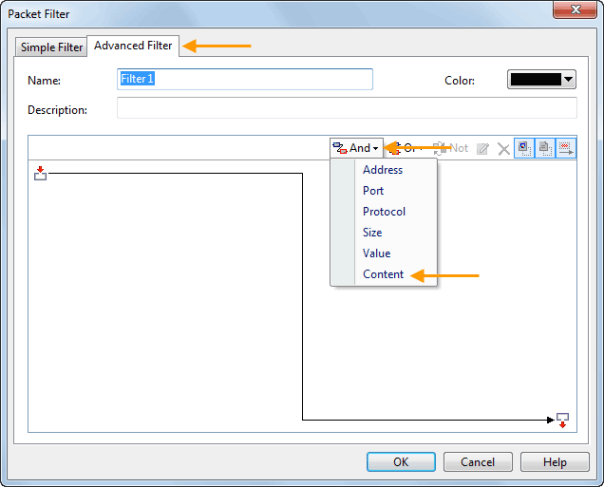
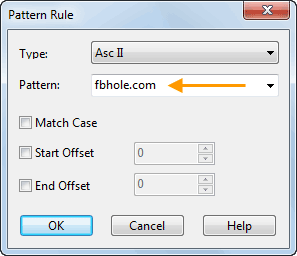
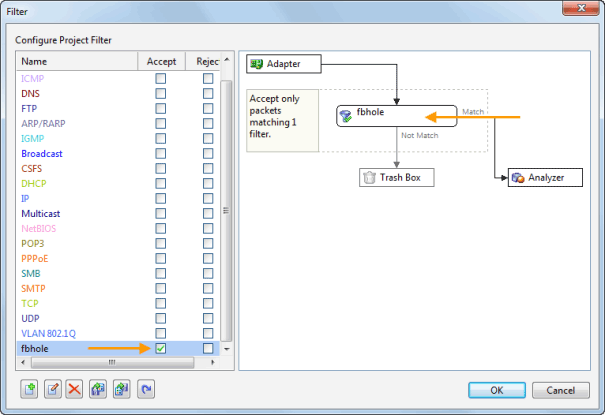
When it comes to network analysis so much is going on that it’s a must to separate out the chatter from the data that matters. Capsa makes it a cinch to hone in on what you want with easy to use filters and rules.
Capsa also has a concept of projects, meaning you can set global filters and rules to always apply but also make specific filters and rules for individual projects, letting you switch between these as needed.
Capsa displays intuitive options and is a genuine pleasure to use. I do not believe I’ve seen a more straightforward or elegant network analysis tool with the majority requiring expert knowledge to get any meaningful results.
Capsa is a commercial product so it does carry a price tag beginning at $US 549 for one license without maintenance but if your job requires you to troubleshoot network faults then the software will pay for itself.
As well as the commercial support Colasoft provide an extensive and helpful FAQ. A free trail of Capsa is avaliable here.