Packet Sniffer Tips: make use of packet size distribution statistics
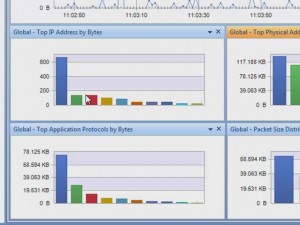
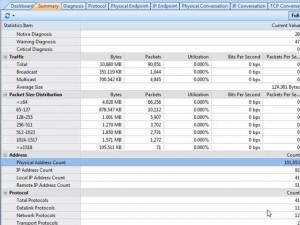
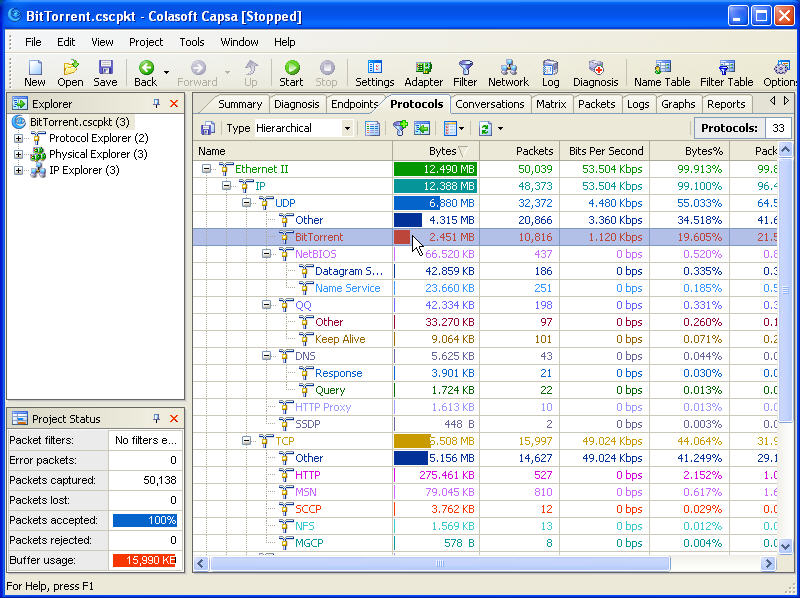
Packet Size Distribution is an important statistic group in the Summary tab in Colasoft Capsa, from which we can get useful information. The Packet Size Distribution group does statistic over seven packet size ranges with their own throughput, packet counting, utilization, and so on. The bigger packet size may result in more Bytes if the packets number equals the ones with smaller packet size. These statistics seem just do simple statistics, but they also give us important information to help us monitor and analyze the network.
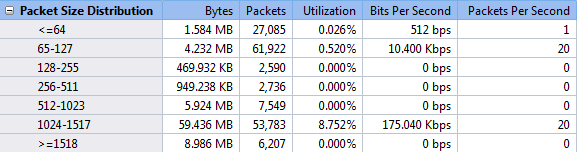
The Packet Size Distribution Statistic Group in Summary Tab
The packet size distribution group can help us manage the network in the following ways:
1. Excessive <=64, 65-127 Packets: Attacks
We know ARP packets are 64 bytes and general TCP STN packets are about 66 bytes. Small sized packets contain less data. A network device needs to spend much of its resource to deal with excessive small sized packets which will result in inefficient to handle normal packets. So if the number is very big than other packet size statistic items, you should be alerted that it might be an attack such as ARP flooding, ARP spoofing, port scanning, worm activities, or DDoS attack.
2. Excessive 1024-1517, >=1518 Packets: Download
With larger size, a packet has a bigger payload to carry more data. That’s why downloading and uploading tools often generate packets with large sizes. These packets are very greedy to consume a big portion of bandwidth. That’s why network administrators always pay much attention to downloading and uploading at workplace. You should keep an eye on this type of packets too.
Note that here we are talking about EXCESSIVENESS, which means the number VERY BIG like tenfold or hundredfold bigger than other counters. Especially the small sized packets and if there is any port scanning on your network, you will capture a big sum of packets of 64 bytes in a blink of an eye and clearly feel the network delay.