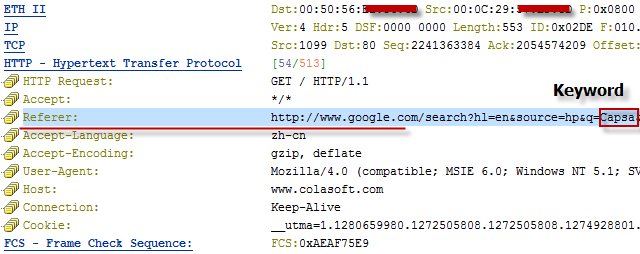
Capsa network analyzer 7.2.1 reviewed by Firewall.cx
Author: Chris Partsenidis
July 3, 2010
Introduction
A Network Analyser is without doubt an Engineer’s best friend.
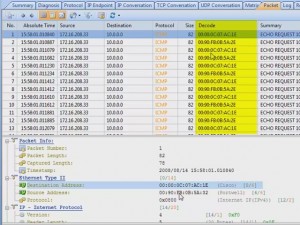
Using network analysing software, we are able to monitor our network and dig into the various protocols to see what’s happening in real time. This can help us understand much better the theoretical knowledge we’ve obtained throughout the years but, most importantly, help us identify, troubleshoot and fix network issues that we wouldn’t be able to do otherwise.
A quick search on the Internet will surely reveal many network analysers available making it very confusing to select one. Some network analysers provide basic functions, such as packet sniffing, making them ideal for simple tasks while others give you all the necessary tools and functions to ensure your job is done the best possible way.
Colasoft’s network analyser is a product that falls in the second category. We had the chance to test drive the Colasoft Network Analyser v7.2.1 which is the latest available version at the time of writing.
Having used previous versions of Colasoft’s network analyser, this latest version we tested left us impressed and does, in fact, promise a lot no matter what the environment demands.
Colasoft’s Capsa network analyser is available as a demo version directly from their website www.colasoft.com. We quickly downloaded the 21.8mb file and began the installation which was a breeze. Being small and compact meant the whole process didn’t take more than 30-40 seconds.
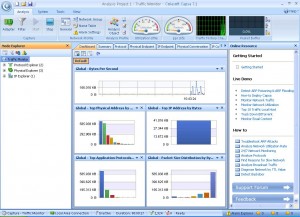
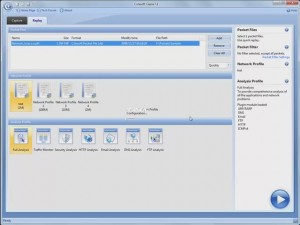
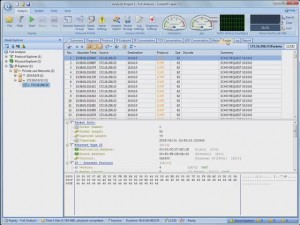
We fired up the software, entered our registration details, activated our software and up came the first screen which shows a completely different philosophy to what we have been used to:
The Software
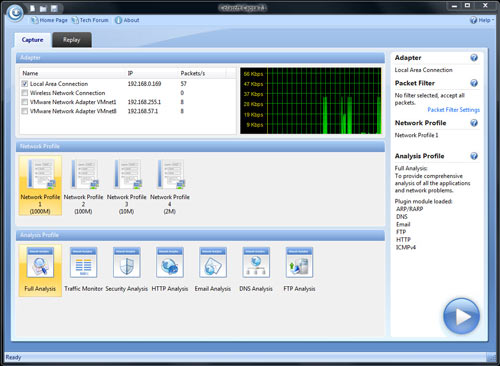
Before you even start capturing packets and analysing your network, you’re greeted with a first screen that allows you to select the network adaptor to be used for the session, while allowing you to choose from a number of preset profiles regarding your network bandwidth (1000, 100, 10 or 2 Mbps).
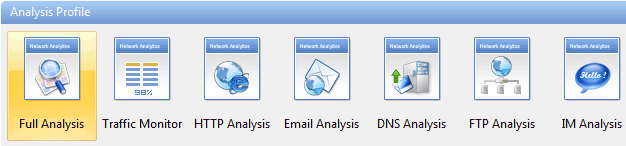
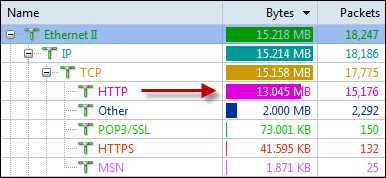
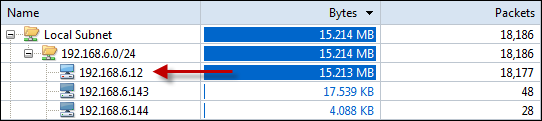
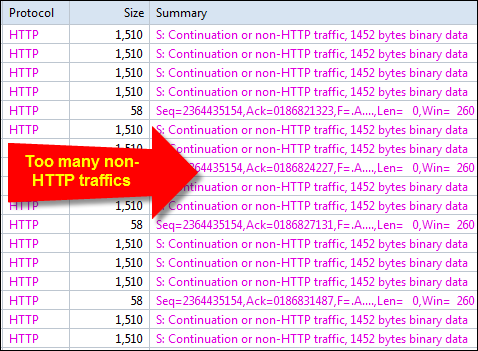
Next, you can select the type of analysis you need to run for this session ranging from Full analysis, Traffic Monitoring, Security analysis to HTTP, Email, DNS and FTP analysis. The concept of pre-configuring your packet capturing session is revolutionary and very impressive. Once the analysis profile is selected, the appropriate plug-in modules are automatically loaded to provide all necessary information.
For our review, we selected the ‘100Mb Network’ profile and ‘Full Analysis’ profile, providing access to all plug-in modules, which include ARP/RARP, DNS, Email, FTP, HTTP and ICMPv4 – more than enough to get any job done!
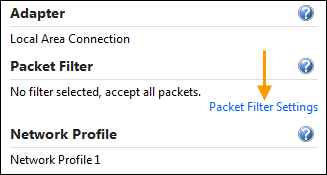
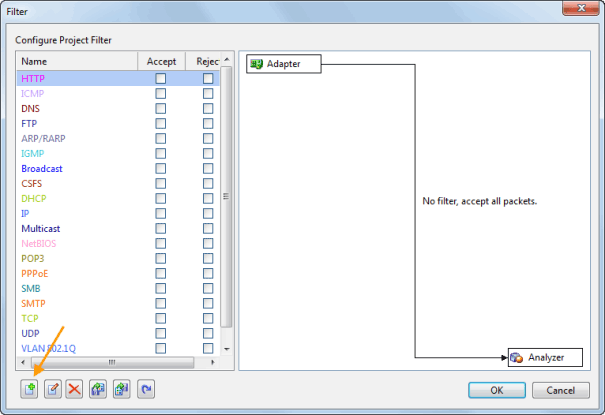
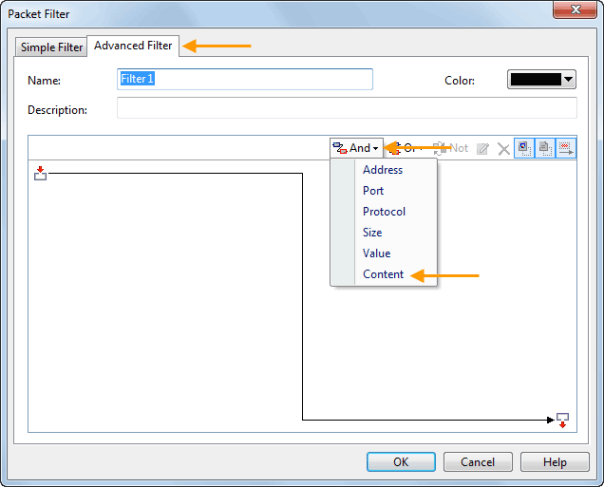
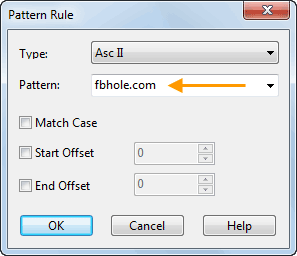
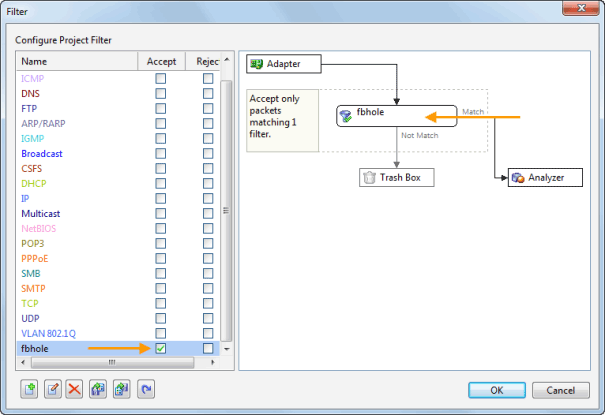
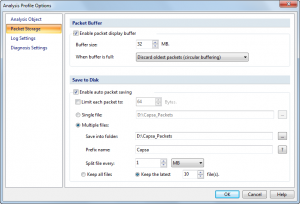
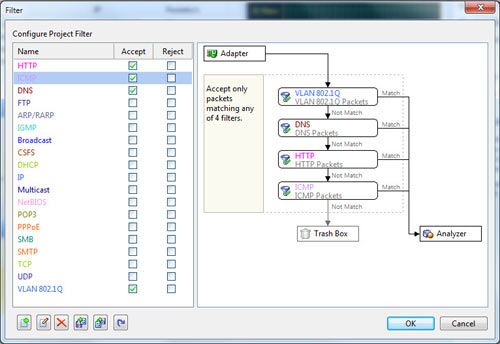
Optionally, you can use the ‘Packet Filter Settings’ section to apply filters to the packets that will be captured:
The full review at http://www.firewall.cx/reviews-colasoft-v721.php