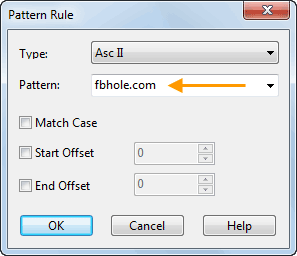
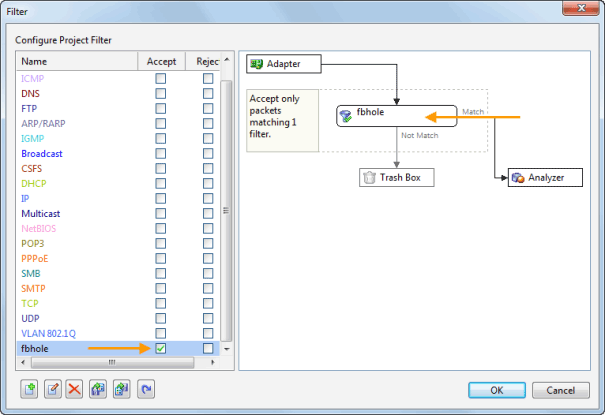
Colasoft Enhances Capsa Network Analyzer with TCP Flow Analysis
We are very excited to release the availability of Capsa Network Analyzer7.5. Except for the enhanced user interface, the biggest highlight of Capsa Network Analyzer7.5 is TCP flow analysis which makes it easier for network administrators to analyze application performance and pinpoint critical performance issues.
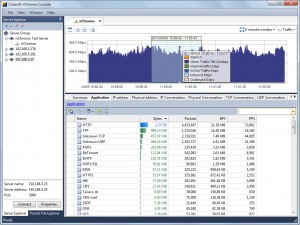
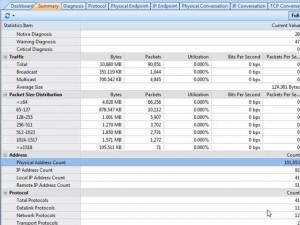
Capsa Network Analyzer 7.5 presents a comprehensive high-level overview of application health on your network. From TCP transaction analysis, you can easily access to more detailed information, including TCP server/client response time, delay, retransmissions, and further down to the server flow to observe the actual media content of the flow. “This unparalleled level of control and visibility speeds time to resolve application problems and minimize overall network downtime,” said Ocean Yu, Vice President at Colasoft.
In addition to MSN and Yahoo Messenger monitor, Capsa Network Analyzer 7.5 added ICQ monitor to meet the market demands. ICQ logs can be easily found at the log tab where detailed information is vividly displayed. Moreover, RADIUS protocol is supported as a new member in the more than 300 protocol analysis family.
Top Highlights of Capsa Network Analyzer 7.5:
1. Powerful TCP flow analysis for application performance optimization
2. Add ICQ monitor to analyze and log ICQ activities
3. Support RADIUS protocol analysis
4. Intuitive TCP transaction sequence diagram
5. Enhanced user interface & performance
Capsa 7.5 runs under Windows XP/2003/2008/Vista/7. A trial version is available for download.