How to Detect MAC Flooding Attack in your LAN?
In a typical MAC flooding attack, a switch is flooded with packets, each containing different source MAC addresses. The switch records these addresses to its CAM table. When the table is full, the switch cannot look up the right destination port, but to broadcast out on all ports. A malicious user could then use a packet sniffer running in promiscuous mode to capture sensitive data from other computers, which would not be accessible were the switch operating normally.
How to detect if there’s a MAC flooding attack in the network? In this article, I will demonstrate to you with Colasoft Capsa Analyzer.
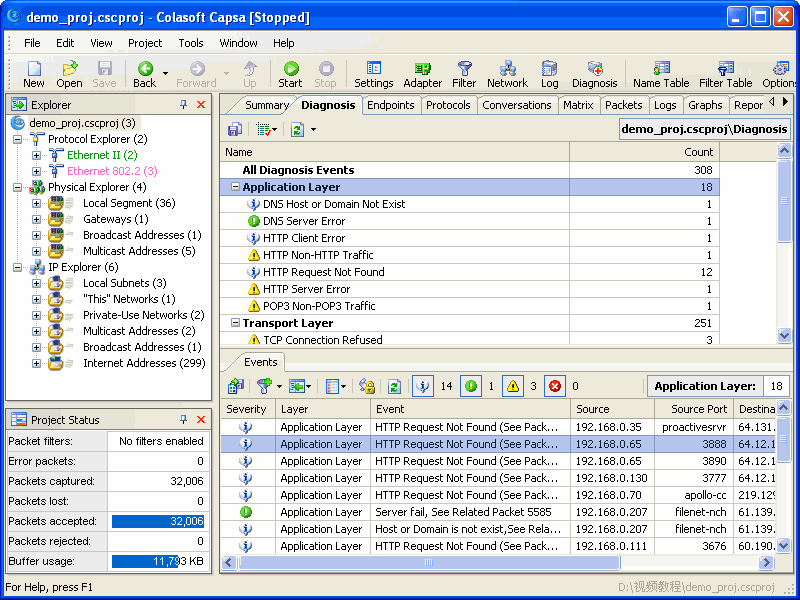
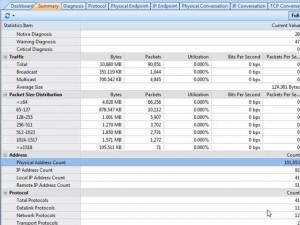
For detecting MAC flooding attack. Let’s start capture, we start the analysis from the SUMMARY TAB. All these statistics seem right. Except one when we come to the Physical address count. There are more than a hundred thousand MAC addresses discovered in this network. How could this small network have so many machines? Possibly, it is a mac flooding attack.
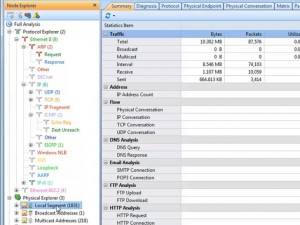
We need to check the addresses in the NOD EXPLORE. Open the physical explorer, and look this number; there are more than 1800 MAC addresses in local segment. It’s abnormal; there is no way that so many machines exist in this network. And apparently, these addresses are not real. We are sure that there are worm activities, or attacks in the network.
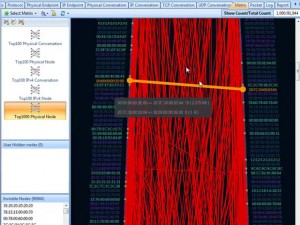
Let’s see how these nodes are communicating. Open the MATRIX TAB. And we choose Top 1000 physical node matrix type. We see this matrix, what a mess! There are so many nodes communicating, and according to the colors of the line, red means one way transmitting.
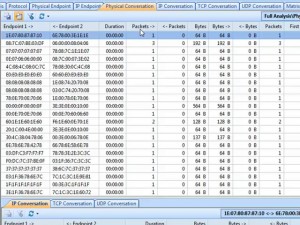
And we can go to the PHYSICAL CONVERSATION TAB to read that it’s true. Almost all nodes only send one packet out. Most packets are 64 bytes.
We know that all machines in our network are connected with a switch. This looks like a MAC flooding attack.
Still, to confirm our prediction, we need to see the original data of the packets they send out. Open the PACKET TAB. We see the delta time between packets is very small, which gives a great pressure to the switch. Almost all packets are 64 bytes. And let’s look at the original data in the packets. Almost all packets are randomly generated by padding same digits in the packets.
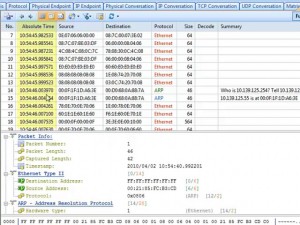
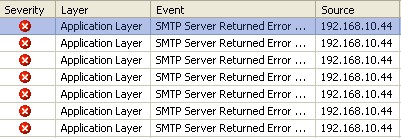
According to all these behaviors, and decoded information from packets, we are pretty sure that there is MAC flooding in this network. But it’s hard to find the attacker’s address directly because all addresses are forged. However, we can cut some machines off the network to eliminate the innocent machines until we find the target one.
Watch the video tutorial of detecting MAC flooding attack is avaliable at Here!