Source: http://www.firewall.cx/cisco-technical-knowledgebase/cisco-switches/940-cisco-switches-span-monitoring.html
Being able to monitor your network traffic is essential when it comes to troubleshooting problems, performing a security audit, or even casually checking your network for suspicious traffic.
Back in the old days, whenever there was a need to monitor or capture network traffic, a hub would be introduced somewhere in the network link and thanks to the hub’s inefficient design, it would copy all packets incoming from one port, out to all the rest of the ports, making it very easy to monitor network traffic. Those interested on hub fundamentals can read our Hubs & Repeaters article.
Of course switches work on an entirely different principle and do not replicate unicast packets out every port on the switch, but keep them isolated unless it’s a broadcast or multicast.
Thankfully, monitoring network traffic on Cisco Catalyst switches is a straight forward process, and does not require the presence of a hub. The Cisco method is called Switched Port Analyser also known as SPAN.
Understanding SPAN Terminology
- Ingress Traffic: Traffic that enters the switch
- Egress Traffic: Traffic that leaves the switch
- Source (SPAN) port: A port that is monitored
- Source (SPAN) VLAN: A VLAN whose traffic is monitored
- Destination (SPAN) port: A port that monitors source ports. This is usually where a network analyser is connected to.
- Remote SPAN (RSPAN): When Source ports are not located on the same switch as the Destination port. RSPAN is an advanced feature that requires a special VLAN to carry the monitored traffic and is not supported by all switches. RSPAN explanation and configuration will be covered on another article.
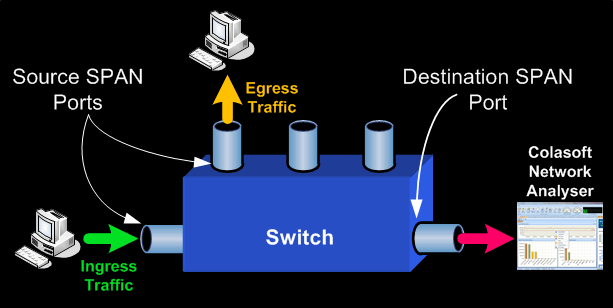
The network diagram above helps us understand the terminology and implementation of SPAN.
Source SPAN ports are monitored for received (RX), transmitted (TX) or bidirectional (both) traffic. Traffic entering or exiting the Source SPAN ports are mirrored to the Destination SPAN port. Typically, you would connect a PC with a network analyser (we trust and use Colasoft’s Capsa Enterprise) on the Destination SPAN port, and configure it to capture and analyse the traffic.
The amount of information you can obtain from a SPAN session really depends on how well the captured data can be interpreted and understood. Tools such as Capsa Enterprise will not only show the captured packets, but automatically diagnose problems such as TCP retransmissions, DNS failures, slow TCP responses, ICMP redirect messages and much more. These capabilities help any engineer quickly locate network problems which otherwise could not be easily found.
Basic Characteristics and Limitations of Source Port
A source port has the following characteristics:
- It can be any port type, such as EtherChannel, Fast Ethernet, Gigabit Ethernet, and so forth.
- It can be monitored in multiple SPAN sessions.
- It cannot be a destination port (that’s where the packet analyser connects to)
- Each source port can be configured with a direction (ingress, egress, or both) to monitor. For EtherChannel sources, the monitored direction applies to all physical ports in the group.
- Source ports can be in the same or different VLANs.
- For VLAN SPAN sources, all active ports in the source VLAN are included as source ports.
Basic Characteristics and Limitations of Destination Port
Each SPAN session must have a destination port that receives a copy of the traffic from the source ports and VLANs.
A destination port has these characteristics:
- A destination port must reside on the same switch as the source port (for a local SPAN session).
- A destination port can be any Ethernet physical port.
- A destination port can participate in only one SPAN session at a time.
- A destination port in one SPAN session cannot be a destination port for a second SPAN session.
- A destination port cannot be a source port.
- A destination port cannot be an EtherChannel group.
Limitations of SPAN on Cisco Catalyst Models
Following are the limitations of SPAN on various Cisco Catalyst switches:
- Cisco Catalyst 2950 switches are able only to have one SPAN session active at a time and can monitor source ports. These switches cannot monitor VLAN source.
- Cisco Catalyst switches can forward traffic on a destination SPAN port in Cisco IOS 12.1(13)EA1 and later
- Cisco Catalyst 3550, 3560 and 3750 switches can support up to two SPAN sessions at a time and can monitor source ports as well as VLANs
- The Catalyst 2970, 3560, and 3750 Switches do not require the configuration of a reflector port when you configure an RSPAN session.
- The Catalyst 3750 Switches support session configuration with the use of source and destination ports that reside on any of the switch stack members.
- Only one destination port is allowed per SPAN session, and the same port cannot be a destination port for multiple SPAN sessions. Therefore, you cannot have two SPAN sessions that use the same destination port.
Configuring SPAN On Cisco Catalyst Switches
Our test-bed was a Cisco Catalyst 3550 Layer 3 switch, however the commands used are fully supported on all Cisco Catalyst 2940, 2950, 2955, 2960, 2970, 3550, 3560, 3560−E, 3750, 3750−E and 4507R Series Switches.
The diagram below represents a typical network setup where there is a need to monitor traffic entering (Ingress) and exiting (Egress) the port to which the router connects to (FE0/1). This strategically selected port essentially monitors all traffic entering and exiting our network.
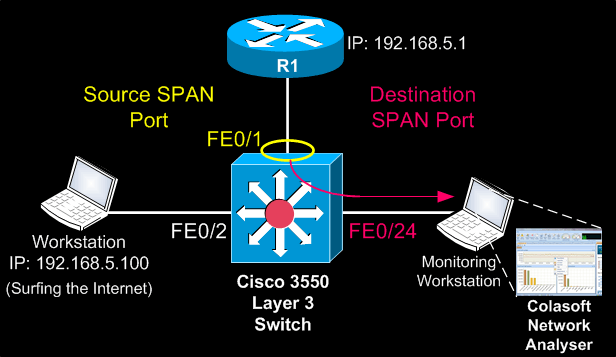
Since router R1 connects to the 3550 Catalyst switch on port FE0/1, this port is configured as the Source SPAN port. Traffic copied from FE0/1 is to be mirrored out FE0/24 where our monitoring workstation is waiting to capture the traffic.
Because serious network procedures require serious tools, we opted to work with Colasoft’s Capsa Enterprise edition, our favourite network analyser. With Caspa Enterprise, we were able to capture all packets at full network speed and easily identify TCP sessions and data flows we were interested in. If you haven’t tried Capsa Enterprise yet, we would highly recommend you do by visiting Colasoft’s website and downloading a copy.
Once we got our network analyser setup and running, the first step is to configure FastEthernet 0/1 as a source SPAN port:
Catalyst-3550(config)# monitor session 1 source interface fastethernet 0/1
Next, configure FastEthernet 0/24 as the destination SPAN port:
Catalyst-3550(config)# monitor session 1 destination interface fastethernet 0/24
After entering both commands, we noticed our destination’s SPAN port LED (FE0/24) begun flashing in synchronisation with that ofFE0/1’s LED – an expected behaviour considering all FE0/1 packets were being copied to FE0/24.
Confirming the monitoring session and operation requires one simple command, show monitor session 1:
Catalyst-3550#
show monitor session 1
Session 1
———
Type : Local Session
Source Ports :
Both : Fa0/1
Destination Ports: Fa0/24
Encapsulation : Native
Ingress: Disabled
To display the detailed information from a saved version of the monitor configuration for a specific session, issue the show monitor session 1 detailcommand:
Catalyst-3550#
show monitor session 1 detail
Session 1
———
Type : Local Session
Source Ports :
RX Only : None
TX Only : None
Both : Fa0/1
Source VLANs :
RX Only : None
TX Only : None
Both : None
Source RSPAN VLAN : None
Destination Ports : Fa0/24
Encapsulation : Native
Ingress: Disabled
Reflector Port : None
Filter VLANs : None
Dest RSPAN VLAN : None
Notice how the Source Ports section shows Fa0/1 for the row named Both . This means that we are monitoring both RX & TX packets for Fa0/1, while the Destination Port is set to Fa0/24.
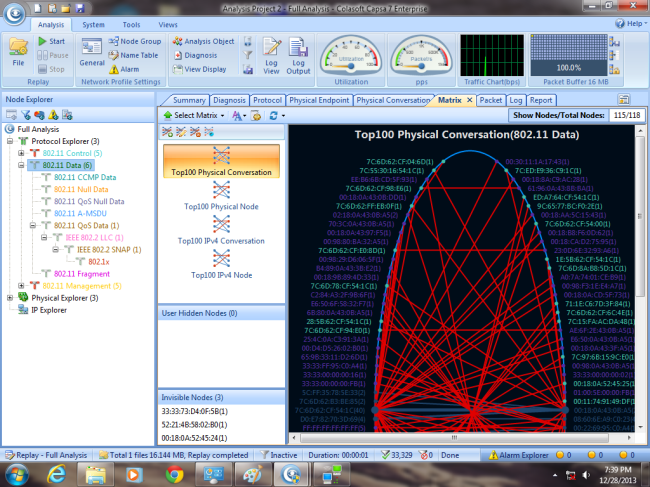
Turning to our Capsa Enterprise network analyser, thanks to its predefined filters, we were able to catch packets to and from the worksation monitored:
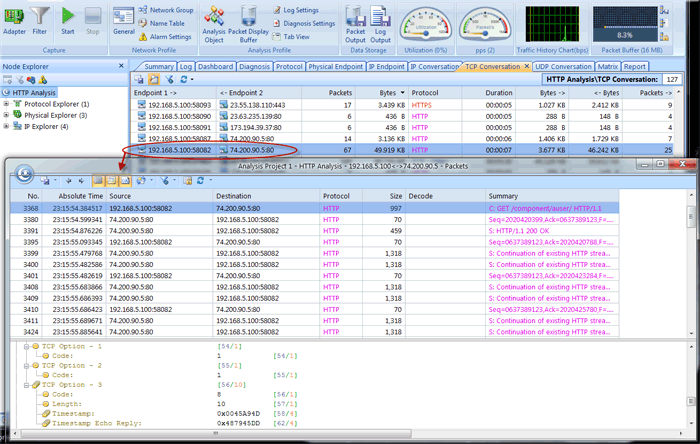
This completes our discussion on SPAN configuration and how to monitor/capture packets on a Cisco Catalyst switch. Upcoming articles will cover RSPAN and more advanced packet capturing techniques using dedicated VLANs for captured traffic and other complex scenarios.