By Shobhan Mandal
Colasoft Capsa Packet Analyzeris a free network analyzer software which can be used toanalyze and monitor WLAN andLAN networks. What it actually provides is network monitoring,in depth packet decoding, andadvanced protocol analysis of the network you are connected to. The best part is you do not have to install this software on a server to view the details; installing in any client machine of the network will provide you with all the necessary details.

Well the software has a number of functionalities, like:
- Troubleshooting Network Problems.
- Know about the performance of the network thus finding any bottlenecks.
- Can be used to detect virus,worms, or network attacks.
- It can also be used to teach and learn various things about network.
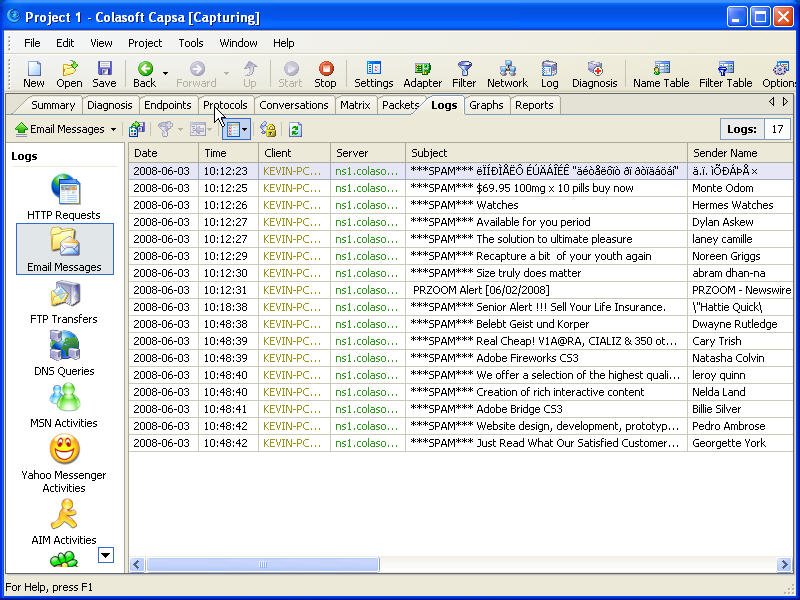
Here we will talk about the free version of Colasoft Capsa which has limited capabilities, like you can monitor the network continuously for 4 hours only using a profile and you can use only 1 analysis at a time.
How to use Colasoft Capsa Free Network Analyzer:
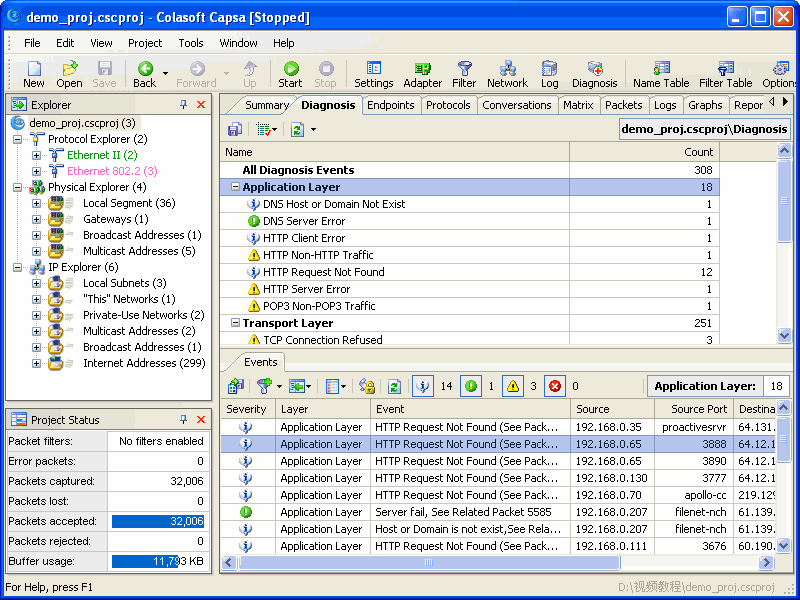
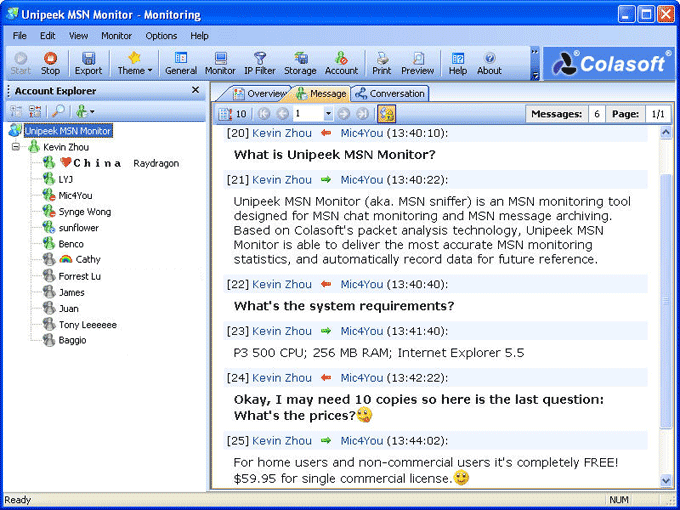
When you are downloading Colasoft Capsa, you will be asked to register with your email address. On this email address, you will be sent activation key, which will be valid for 4 months, after which you have to renew. The installation process will take a minute or two. After the installation is over you will get the home screen which looks like the first screenshot of this review.
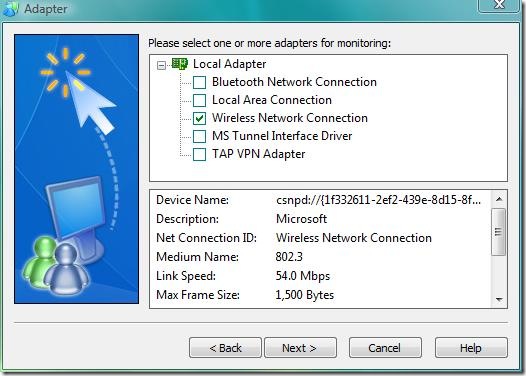
At first, you have to select the connection from the adapter which you would like to monitor. When selected, it immediately shows a graph for the speed of the network.
The profile section allows you to select what type of analysis you would like to do. The software offers:
- Full Analysis
- HTTP Analysis
- Email Analysis
- DNS Analysis
- FTP Analysis
- IM Analysis
- Traffic Monitor
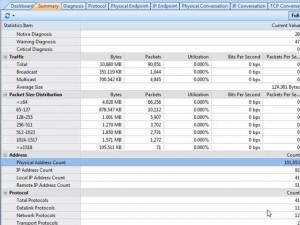
Full Analysis
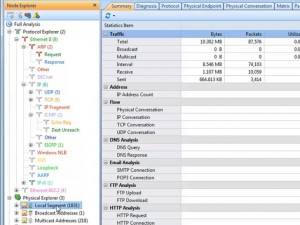
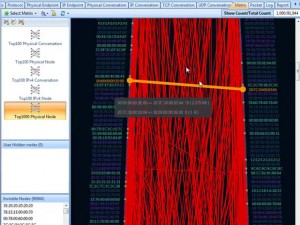
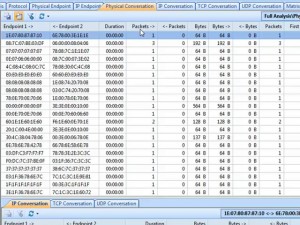
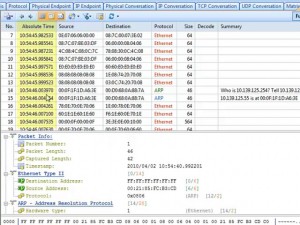
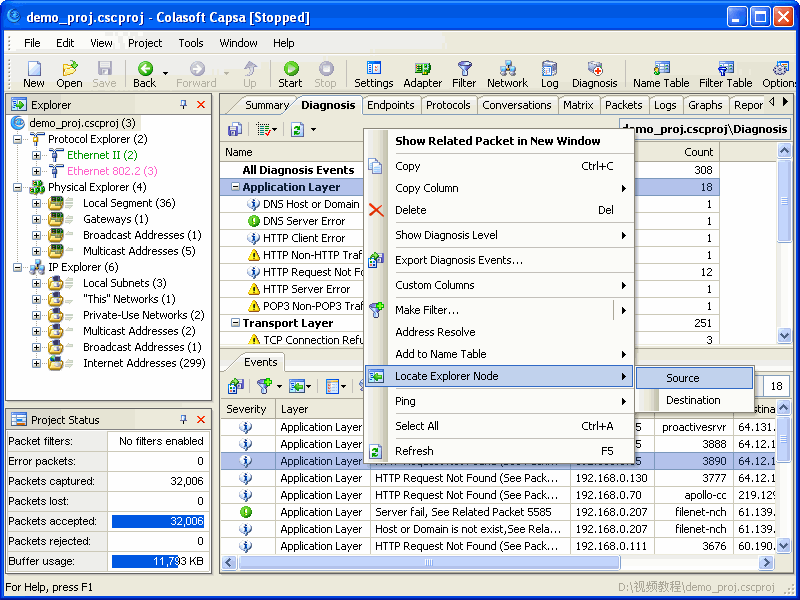
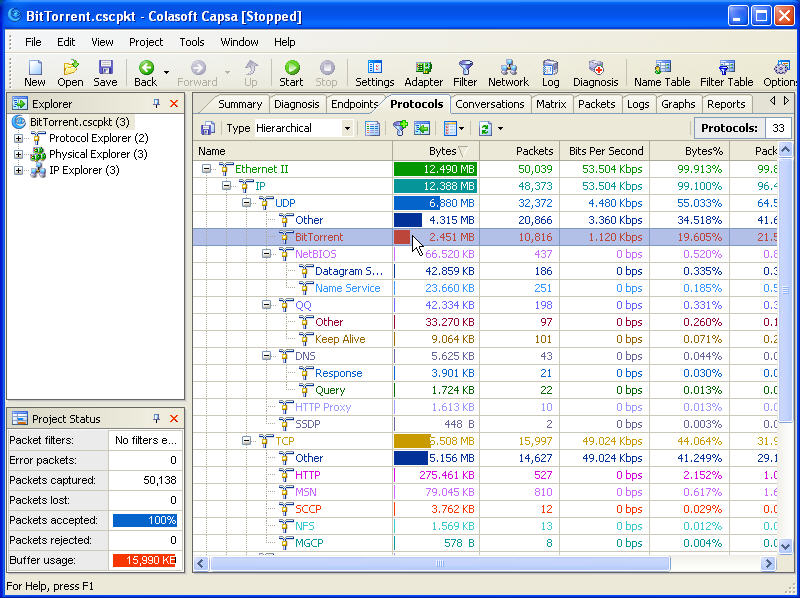
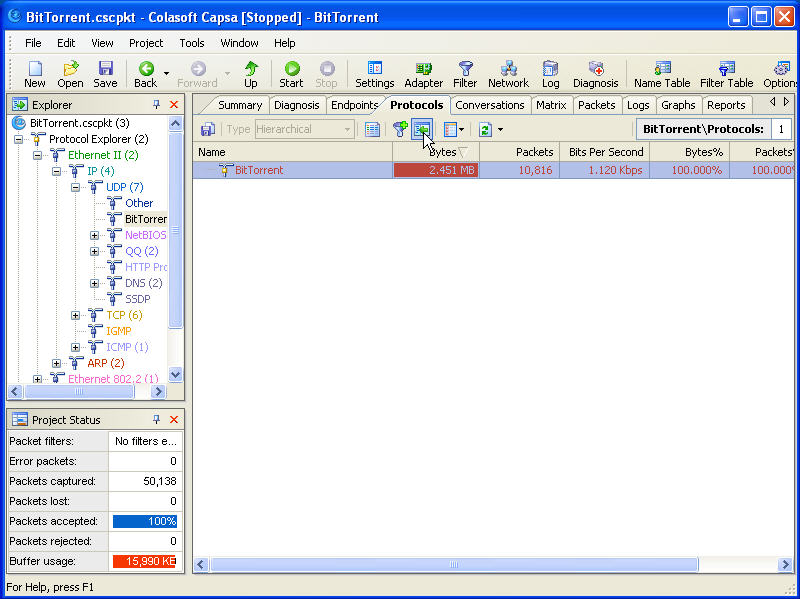
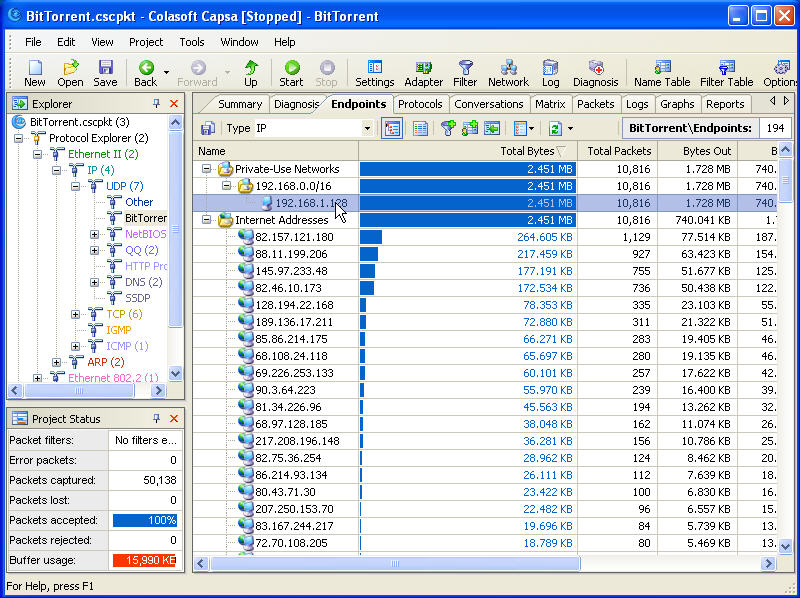
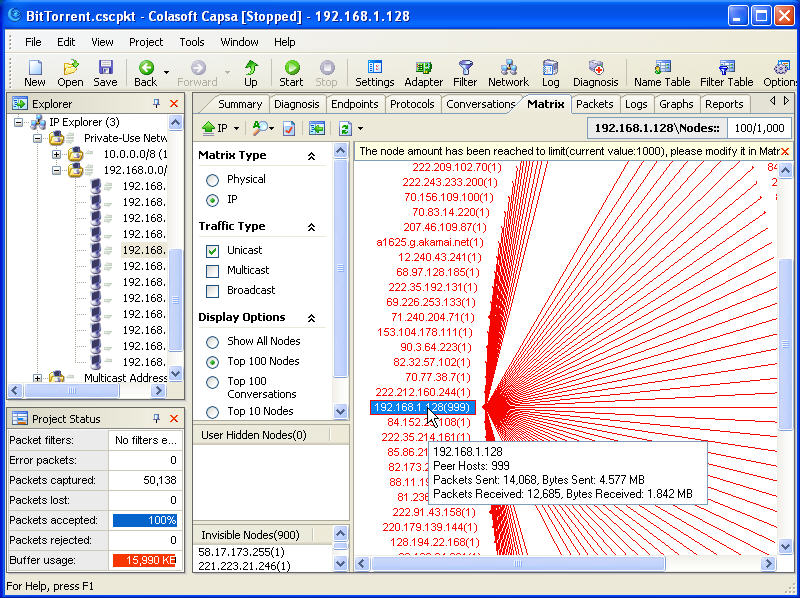
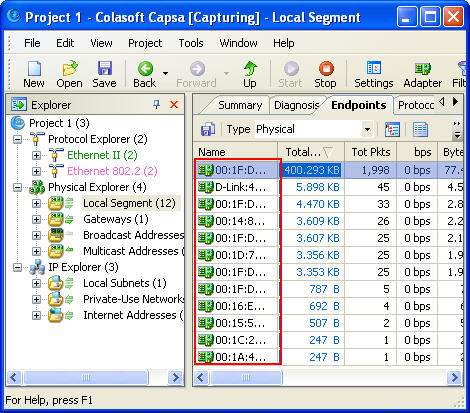
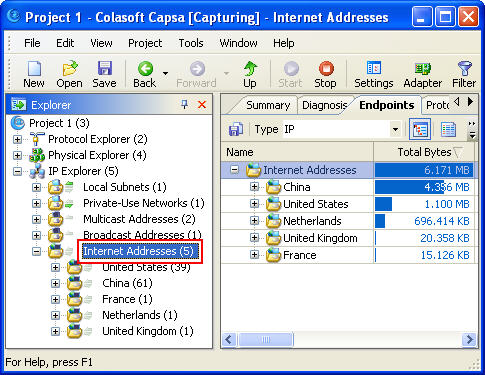
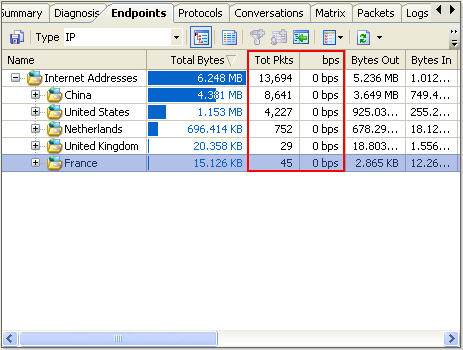
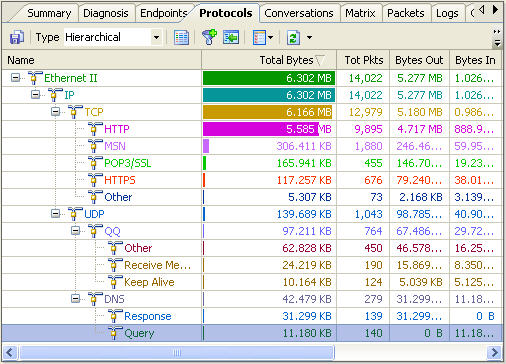
Clicking on Full Analysis gives you various information regarding broadcast addresses, multicast addresses, local subnet, the IP addresses of the computer connected, etc. The center screen has various tabs like Protocol- tells about different protocols like IP, ARP, IPv6 and the amount of data and packets being transferred.
Physical Endpoint, IP Endpoint which tells about the MAC address and the IP address of the connected systems. Other tabs include TCP, IP, and UDP conversations. Somefunctionalities may not work in the free version.

HTTP Analysis
The HTTP analysis gives you the various results regarding HTTP protocol. At any normal instance it will give the IP address of the computers with which your computer has a HTP connection. Through the IP, TCP, and UDP conversation you can know the amount of data and packets being shared among the computers.

The other analysis gives out more information regarding data and packet movements in the network you are connected to.
Talking to one of my friends who is a ethical hacker and wants to remain anonymous, said that the software is great. According to him:
- This is really a great software and very powerful.
- It helps the network administrator to get various details about the network in real time.
- It can be used for educational purposes as the software tells how packet movement works actually in the network.
Downsides of the software
In the free version, the user cannot use more than one analysis simultaneously. If he wants to have a different analysis he must close the ongoing analysis. The free version has most of the good features restricted not allowing users to know the software’s working properly.
Also check out other network packet sniffer software.
Conclusion
It is a cool software to monitor the data traffic of your network. If you setup a private network you can watch out for any wrongdoings that might happen be happening in the network. It is very much useful for those who want to know more about computer networking.
Get Colasoft Capsa Packet Analyzer here.

![]() to set which time period to show:
to set which time period to show: